Youtubeᴾˡᵘˢ Super Assistant(Video Downloader & 🚫 No ads & New Layout For YT!) 2025-07-24 被举报,原因为:其他
in response to the moderator closing my last report with the question:
This report has been dismissed by a moderator.
proof?
here is the proof:
if you click on the download button provided by the script for a video, it redirects you to the website, tikfork.com here is an example:
https://www.tikfork.com/en/yt?s=1&url=https://www.youtube.com/watch?v=T5UpyJVr-9s
in the script its obfuscated.
it’s not immediately obvious because it’s buried in a dynamically created .
Here’s what’s happening:
In the script, there’s a function called createIframe() that builds an invisible iframe and appends it to the page.
That iframe’s src is set to https://www.tikfork.com/en, and it’s triggered when the user clicks the Download button.
The iframe is styled to be hidden (display: none), so it doesn’t visibly load anything—but it still initiates a request to that site.
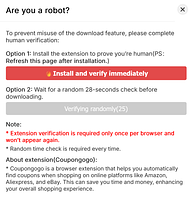
when clicking a link to download the file on the page, it requires you to install an extension:
{About extension(Coupongogo):
* Coupongogo is a browser extension that helps you automatically find coupons when shopping on online platforms like Amazon, Aliexpress, and eBay. This can save you time and money, enhancing your overall shopping experience.}
The extension itself (Coupongogo) is marketed as a coupon finder, but in this context, it’s being used as a gatekeeper—you’re forced to install it before accessing the actual download functionality.
Even if the extension isn’t outright malware, it’s likely part of a traffic monetization scheme that compromises user experience and privacy:
The developer admits to using an affiliate program
it Allows access to all websites, posing a significant security risk as it can monitor and modify data from any visited site.
it uses both clipboard and unlimited storage permissions
in addition, the user 'funnymonkey' who makes this extension has one other extension to his name on firefox:
Enhancer for YouTube - which is according to the comments is identical to this script.
the whole thing is an affiliate marketing scam, which certainly must break some rule. deceptive at best.
I just saw this report again, and honestly, I feel helpless. Let me clarify things carefully here: 1、The report claims that the script contains a createIframe() function. Where is it? It’s very clear that no such function exists in the script (the code is open and easy to inspect). 2、Regarding the video download feature, a popup clearly informs the user when it's used for the first time that it will redirect to a third-party website. The functions of that third-party site are beyond the control of this script. Users can choose whether to use the feature or completely disable it (there is a related toggle in the script settings).Furthermore, the description section of the script also explains this clearly. I don't understand why the reporter refuses to read this carefully. 3、This script only runs on YouTube-related websites (verifiable from the code). It does not have the ability, nor does it attempt, to collect any user data. 4、The reporter keeps mentioning an extension called "Coupongogo". I have no idea what this extension is or what it does. What does it have to do with me or my script? This seems completely absurd. 5、The script code is not minified or obfuscated. It is released under the MIT license and is fully open-source — anyone can freely use or modify it. This script was written strictly according to GreasyFork's rules, and its functionality has been described clearly and transparently. I truly feel helpless in the face of this kind of report.
此次举报提交后,此脚本已被更新。
Zephyros(被举报用户)已有:
管理员已通过该举报。
Find a different way to download videos, this extension looks fishy.